
Github Secrets: A Complete Guide

If you chose GitHub like 90+ million developers and 4+ million organizations, you might have heard of their CI/CD automatization workflow service: GitHub Actions. Github Actions relies on Github Secrets to handle sensitive environment configuration parameters. You often need environment variables to configure your devops pipeline: API keys, database passwords, login credentials… you name it. Github Secrets allows developers to store this information securely and effecively. In the following article, we are going to see how to use secrets with your Github repository.
What’s A Github Secret
A secret is a sensitive piece of data used to access or configure a service. For example, you need an email and a password to log in an application and perform actions―these are secrets!
Secrets can also be environment configuration variables: database credentials (a database URL), API keys, token signatures… Secrets are sensitive, meaning they need security systems to protect them from being displayed to a third-party. This is where Github Secrets come in.
Here’s an example of a Github Actions configuration file using a secret named “SECRET_ENV_VAR”:
steps:
- name: test
env: # Or as an environment variable
SECRET: ${{ secrets.SECRET_ENV_VAR}}Why Github Secrets
-
No more hardcoded secrets - Github Secrets gives you a simple solution to avoid harcoding secrets in your codebase. Hardcoding secrets can lead to major security leaks. Not only will it cost a lot of money to fix, but as the one responsible for leaking your companies’ secrets you can also be fired or even sued. Using tools like Github Secrets or Onboardbase will protect you from security risks.
-
No more .env files - Developers use .env files to store secrets in environment variables, avoiding to hardcode them. But .env files can leak if you forget adding them to your .gitignore, or if a misconfigured web server exposes them to the public. Just like hardcoded secrets, .env files can lead to major leaks. With GitHub Secrets, you can get rid of .env files because secrets are directly available as environment variables.
-
Let GitHub encrypt the secrets for you - Wherever you store your secrets, you need to encrypt them. Keeping your secrets encrypted protects you, to some degree at least, against breaches. Even if an attacker obtains them, they are useless without the decryption key. Github keeps secrets encrypted, and collaborators who will use them won’t even need to know their value to do so.
How To Use Github Secrets: 6 Simple Steps
1. Create a new Github repository
If you don’t already have a Github repository, create a new one to host your Github Actions workflow:
git initIn Github, create a new private Github repository and go back to the command line with the URL of your new repository:
git branch -M main
git remote add origin <your repo's URL>2. Create a new Github Personal Access Token
You’ll need a Github personal access token (PAT) to access Github’s API from the command line.
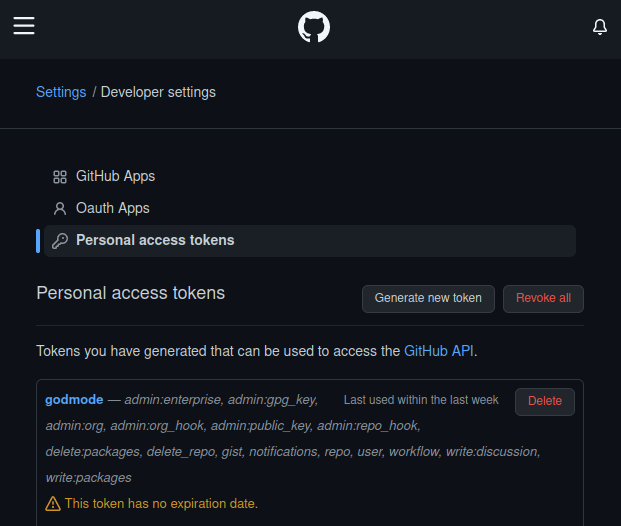
Go to your Github account and click on Settings > Developer Settings > Personal Access Tokens. Press the button “Generate new token”. Just make sure to check Workflow in the list of scopes and you’re good to go.
3. Create a workflow file
A GitHub Actions configuration file contains a list of commands to run on specified git events. It can be used to setup and configurate all stages of the CI/CD pipeline.
- Create a .github/workflows folder in your repository.
- In this folder, create a .yml file. For example : “github-actions.yml”
- This file will contain the instructions for your workflow:
name : GitHub actions test
on : [push]
jobs :
test :
run : echo "test"For example, this script will display the word “test” every time a “git push” event is registered.
4. Adding secrets to Github
GitHub uses Libsodium sealed boxes to ensure the secrets are encrypted before they reach GitHub. Secrets remain encrypted until they’re used in the workflow.
To create secrets for a personal account repository, you must be the repository owner. To create secrets for an organization repository, you must have admin access.
- On GitHub, get on your repository’s page
- Click Settings > Secrets > Actions > New repository secret
- Give a name to your secret (see documentation for naming secrets)
- Enter the value of your secret (token signature, API key, DB credentials etc.)
- Click Add secret
5. Use Onboardbase to handle your encryption and management of secrets
Onboardbase is a solid alternative to GitHub Secrets that focuses on team collaboration.
Each teammate can be given permission to use secrets based on their role in the organization. Onboardbase is based on a principle of least privilege, so invited teammates will only be given the secrets they need. No more, no less.
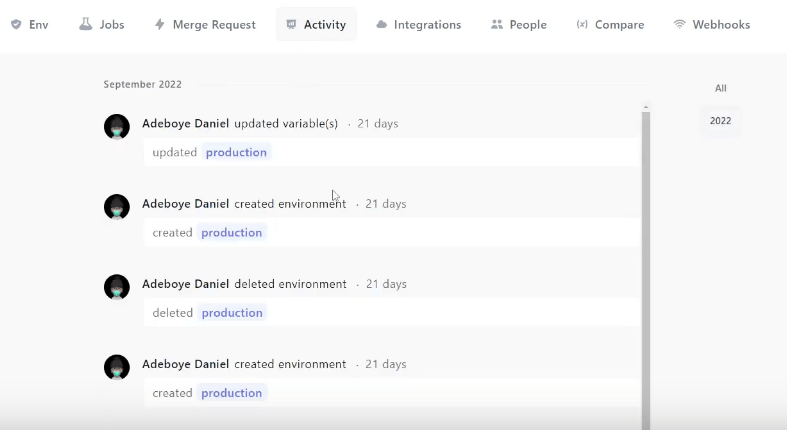
Keeping track of what’s going on with each secrets is also extremely easy to do with Onboardbase. Just use the Job and Activity sections to keep track of your secrets’ usage:
More importantly, you can easily use Onboardbase in any GitHub Actions workflow. Here’s how:
1. Create a new secret on Onboardbase.
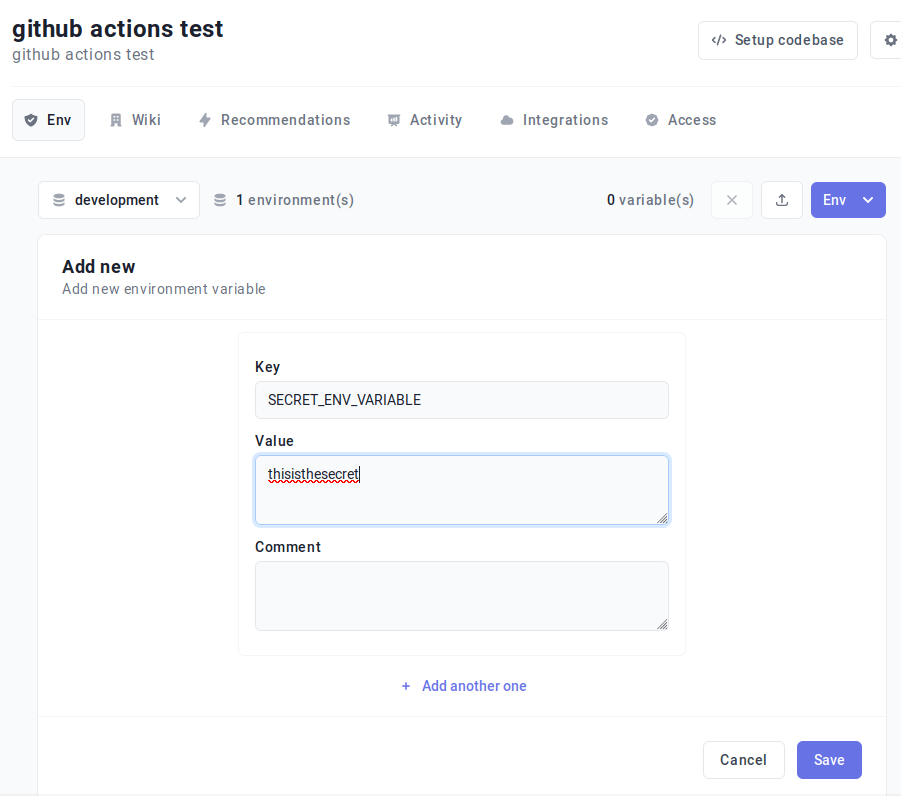
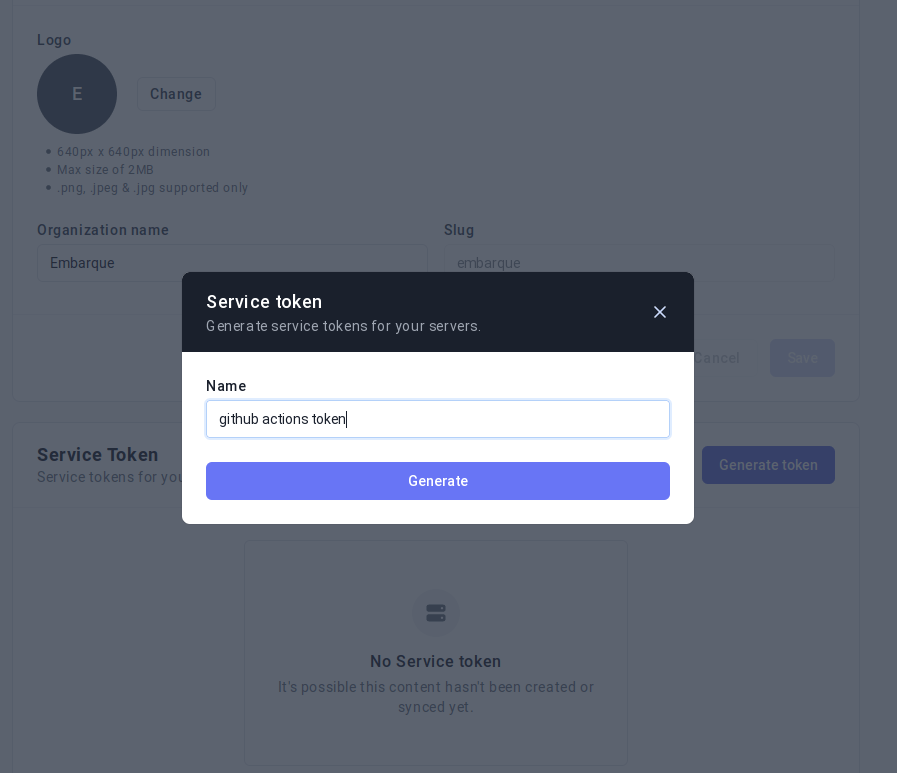
2. Create a service token.
Go to Settings > Manage your org > Service Token and generate a new service token to authenticate with Onboardbase from Github Actions.
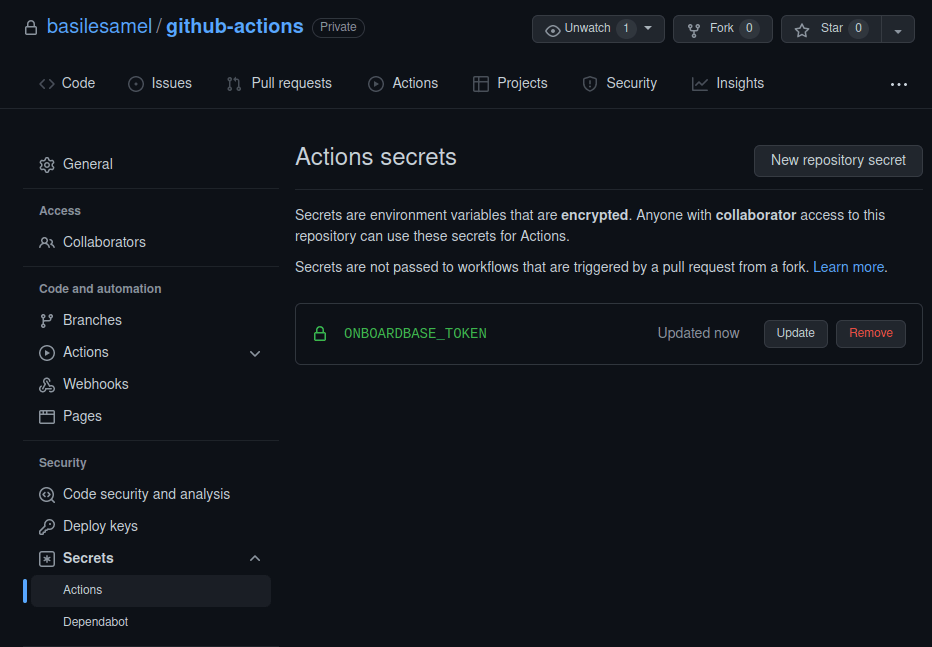
3. Add your Onboardbase token to Github Secrets.
Go to your Github repository, click on Settings > Security > Secrets > Actions, and add your Onboardbase token:
4. Update your workflow configuration file.
We add 3 steps to the workflow to inject variables at run time:
name : GitHub actions test
on : [push]
jobs :
test :
env :
SECRET_ENV_VARIABLE : test
steps :
- name : Download Onboardbase
run : wget https://onboardbase-cli.fra1.digitaloceanspaces.com/apt/onbardbase.deb
- name : Install Onboardbase
run sudo dpkg -i onboardbase.deb
- name : Setup Onboardbase
run : onboardbase config:set --token "${{secrets.ONBOARDBASE_TOKEN}}"
- name : Run project
run : onboardbase build -c "printenv SECRET_ENV_VARIABLE" --project "github actions test" -e "development"First, we install Onboardbase’s debian package to the Github Actions server, then we use our Onboardbase token stored in Github Secrets to automatically configure your project environment variables. It’s the only credential you’ll need to deal―pretty convenient!
Finally, we run Onboardbase’s CLI build command to run scripts. The program prints the value of SECRET_ENV_VARIABLE stored in Onboardbase: “thisisthesecret”:
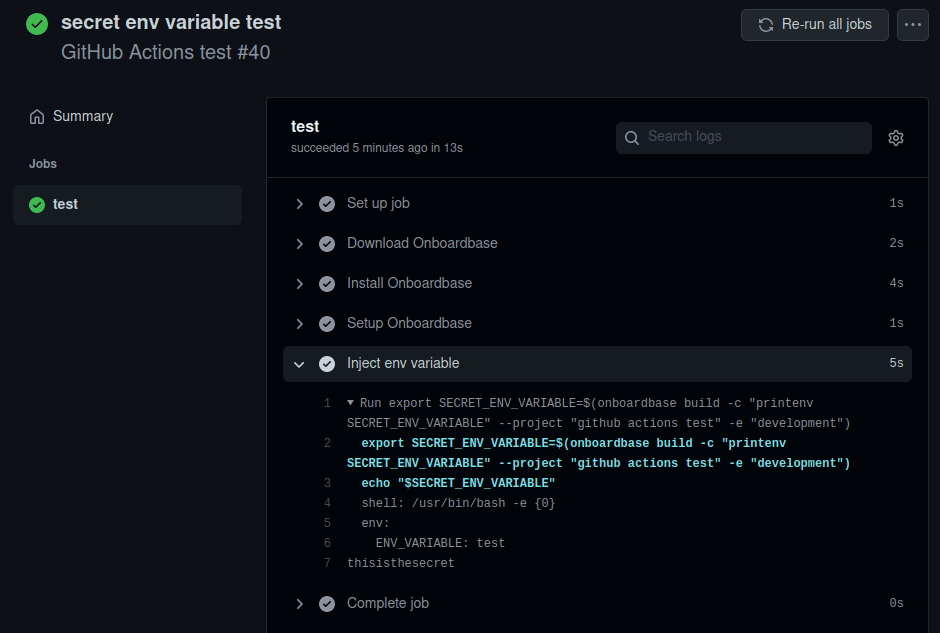
With Onboardbase, you can inject secrets in any projects, so you don’t have to re-define environment variables from one repository to the other unless you chose to. Again, this prevents us from hardcoding secrets, leaking .env files, and storing secrets as plain text.
Whatever your tech stack, Onboardbase has got you covered. Check our documentation to setup Onboardbase secrets.
Use Onboardbase to protect your environment config
We showed you what GitHub Secrets are, how to use them, but also why they are limited for collaboration and how they lock you in a platform.
With Onboardbase, you can use an intuitive and easy to use collaborative approach to secrets management and use your encrypted secrets for any project. With our documentation and videos on our Youtube channel, teams get set up within 15 minutes. Try it for yourself for free or book a demo with us if you need help to set up or for further insights on features we offer.
Subscribe to our newsletter
The latest news, articles, features and resources of Onboardbase, sent to your inbox weekly