
The Only 4 Secret Management Tools You'll Need In 2023: Tips, Tricks & Examples

At Onboardbase, we know how hard it is to keep your secrets safe. Even huge companies leak secrets from time to time: Github exposed a private SSH key no later than March 2023 by pushing it to a public repository. It’s even harder for startups because you lack time, funds, and people, by definition.
Fortunately, there are plenty of solutions to help you manage your secrets in 2023. But what cybersecurity experts don’t tell you is you don’t need dozens of tools to do the job: only four suffice, because security doesn’t have to cost an arm.
In this article, we’ll dive into what secret management really is, why it’s essential for a startup, and why you only need 4 tools to cover all your needs. Let’s go!
What’s Secret Management
Secret management is the process of securing sensitive information used in software development, like credentials, API keys, and certificates, throughout the entire lifecycle.
For example, a static website built using a third-party CMS service might need to perform an API call at build time. Secret management handles the API key management in both development and production environment as part of the CI/CD pipeline, ensure best practices are implemented to prevent unauthorized access to the API key, and stores the sensitive information in an encrypted vault that only a select few employees can update.
As a startup, chances are you interact with secrets on a daily basis, sometimes even without noticing it. And since these secrets are important, you need ways to protect them from harmful behaviors.
Why Secret Management
Secret management should be an integral part of any startup’s development workflow for three main reasons:
- Legal compliance - Startups need to comply with various regulations requiring the protection of sensitive customer data, like GDPR in Europe. Secret management deals with some compliance standards automatically, reducing the risk of costly penalties or legal actions: a data breach costs $9M in the US on average!
- Software Security - 50% of large enterprises spend at least $1M per year on cybersecurity, while smaller companies spend less than $500 per year, making them an easy target for attackers. When you compare what it costs and how much it reduces the attack surface of your software―stolen credentials are the most common cause of data breach―secret management is a high return-on-investment practice to protect sensitive data from unauthorized access, theft, or misuse, reducing the risk of data breaches and other security incidents.
- Improved Collaboration - As a startup, you often work with partners, contractors, and other third-party services who may need access to sensitive information. Secret management enables secure secret sharing with authorized parties, allowing startups to build faster without compromising the security of their data.
What You Need For Secret Management
Secret management can be divided into 6 key components:
- Secret generation - Generating strong and unique secrets is critical.
- Secret vault storage - Securely storing secrets.
- Code scanning - Regularly scanning for vulnerabilities in secret storage systems helps to identify potential security risks or weaknesses like misconfigured access controls, weak encryption, or other vulnerabilities that could be exploited by attackers.
- Secret sharing - Startups may need to share secrets with partners, contractors, or other third parties, making secure sharing critical.
- Secret distribution & delivery - Secrets need to be delivered securely to applications or users that require them.
- Monitoring & alerting - Monitoring secret access and usage to detect unauthorized access or misuse of sensitive data.
Let’s detail each component with its challenges and solutions to better understand how to protect your startup.
1. A Custom Strong Secret Generator
Using strong secrets is the first (and perhaps most important) step to keep the whole system secure. Generating secrets like passwords manually is a no-go because they can contain biases that can be easily exploited by attackers: they are either too simple to guess, too random to remember, or too time-consuming to scale well to dozens of online services.
Effective secret generation involves:
- Using secure random number generators - Automated secret generation should be the standard in your company policy. All main browsers now include secure password generators.
- Enforcing minimum complexity requirements - A strong secret is a secret that can’t be guessed using brute-force algorithms in a realistic amount of time.
- Avoiding easily guessable secrets - Common passwords like 123456 should be banned from use on your app, using an official list of blacklisted passwords.
If your software product involves using secrets like passwords, make sure to code your generator properly to use a series of numbers, uppercase and lowercase letters, and symbols that’s at least 12 characters long. For example, in Javascript:
import crypto from crypto
const password_generator = () => {
const length = 12
const charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!?,.;/:-=+{}",
let res = "";
const size = charset.length
for (let i = 0 ; i < length ; i++) {
res += charset[crypto.randomInt(size)]
}
return res
}Note that we use the crypto library to generate a random number between 0 and the size of charset, instead of the Math.random function. That’s because the latter isn’t cryptographically secure, which is a key requirement to get random passwords.
2. Secret Storage With Onboardbase
Without a centralized place to store secrets, startups may store secrets in insecure locations (e.g post-its, emails) or rely on inconsistent processes (send API keys in plain text via Slack or a Notion wiki), making it difficult to secure secrets effectively. Since most companies rely on countless third-party services to run their operations, secrets tend to spread out all over the place―creating the perfect security nightmare!
Effective secret storage involves:
- Proper encryption - Secrets should never be stored in plain view, unencrypted.
- Secret rotation - Changing your secrets prevents hackers from using them when you fail to notice a security breach.
- A centralized vault - A central location prevents secret sprawl that could lead to human errors.
Onboardbase addresses all three. It’s a centralized secret management platform that helps startups securely store, share, and manage secrets. The secrets are encrypted at rest using AES-256, and in transit with a combination of RSA and AES-GCM. The web dashboard makes it easy to put all your secrets in a single user interface that’s easy for everyone to access and contribute to, without compromising on access control:
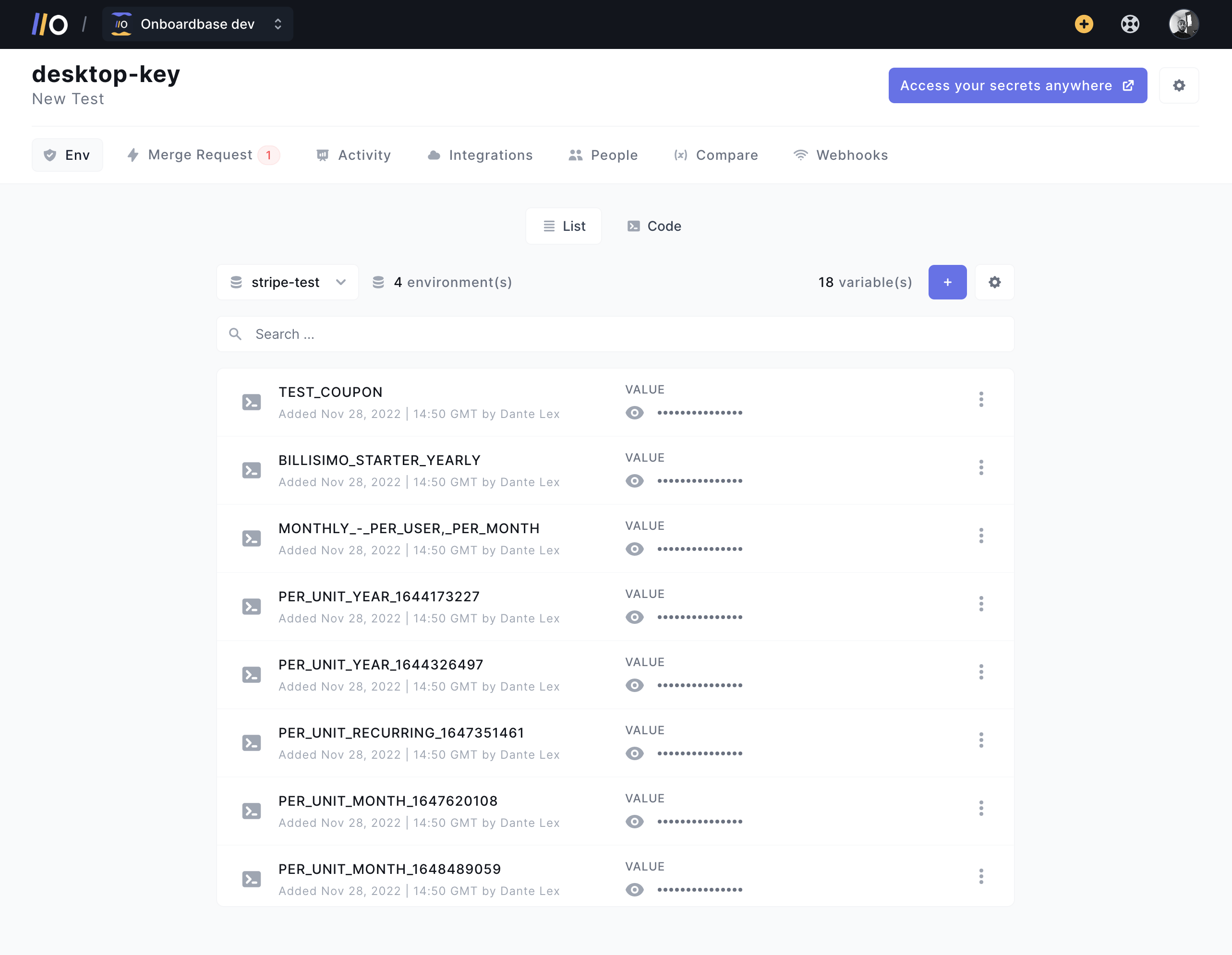
Developers can easily get started with the Onboardbase CLI in one command line in any code repository to store secrets from their terminal. And the API makes it easy to automate secret rotation for any third-party service.
3. Code & Secret Scanning With Github
As startups launch new features and fixes, vulnerabilities can appear because of your own code or third-party dependencies. Vulnerabilities are especially hard to find in huge codebases in the heat of the moment, especially for startups with limited resources. To solve this, automated code scanning detects vulnerabilities as they appear and provide actionable insights to remediate them before they can be used by attackers.
While Onboardbase offers secret scanning as a feature, you can also use Github to scan your entire codebase for vulnerabilities, not just vulnerable secrets.
Code scanning is an enterprise feature, so you’ll need to upgrade your Github account if you need it for private repositories. It’s free for public repositories though.
It’s pretty convenient because you can schedule scans to run automatically on each commit, and the alerts are directly integrated into the Github interface. Since Github is the most popular code repository management tool, it doesn’t require any additional setup to get started.
For extra security, Github is also interoperable with third-party code scanning tools following the SARIF standard via Github Actions.
4. Secret Sharing With Disposable
You always need a proper way to share secrets with teammates for effective collaboration while protecting sensitive data―if you have to run around after every one to get access to a file, you’re losing precious time! But improperly sharing secrets also greatly increases the risk of unauthorized access: stolen credentials are the n°1 cause of security leaks, and phishing comes second with 37% of all cyberattacks.
To address all these challenges, you need secure communication channels to transmit secrets to authorized teammates.
At Onboardbase, we built Disposable: a real-time, end-to-end encrypted, and ephemeral online chat. The messages disappear as they are read, no data is stored or retained, and all data is encrypted in transit using perfect forward secrecy. You just have to send a temporary invite link via email or text and your teammate will be able to view the required credentials right away:
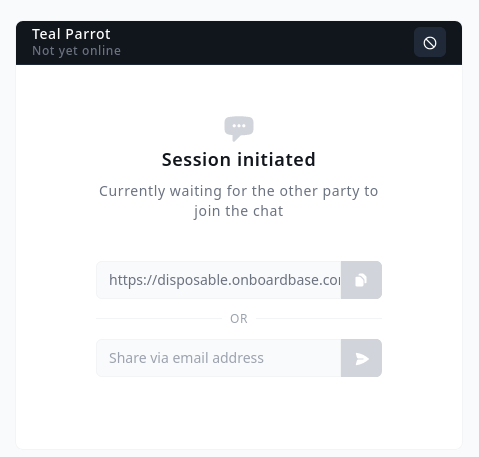
This is perfect for one-time transactions when you don’t want to setup an Onboardbase account for a stakeholder, but it’s strongly advised to prefer in-app invites to leverage role-based access control and secret usage monitoring.
5. Secret Delivery With Onboardbase
Once you have your secrets in a secure vault, you still need a way to seamlessly integrate these secrets in your development workflow.
Instead of hardcoding credentials or using .env files you could leak in your git repository, Onboardbase defines environment variables for all your secrets via CLI. After installing the CLI, all you need is a single wrapper command:
onboardbase run --command="node server.js" -p [PROJECT_NAME] -e [ENVIRONMENT_NAME=development]You can configure the project, the desired environment (development, staging, production, etc), and Onboardbase takes care of the rest, including encrypting and signing secrets during transit via an encryption key stored on your local machine. You can just call environment variables in your code as usual.
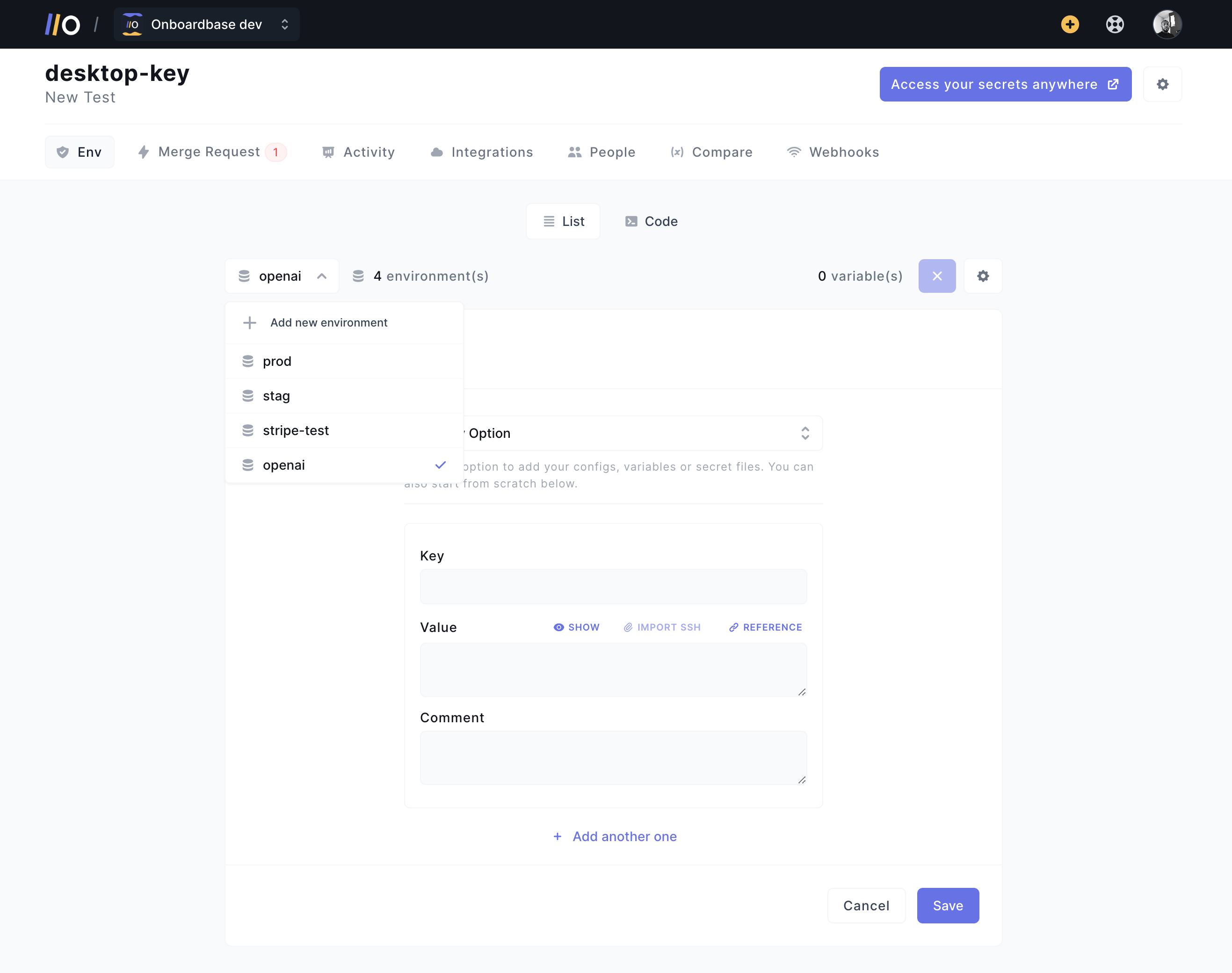
Because there is a lot of devops solutions out there, Onboardbase also sports plenty of integrations to choose from, including AWS Lambda, Github, Cloudflare Workers, and Firebase Functions.
Last but not least, the access control interface is designed for modern development teams: you can define role permissions by user or by group, revoke accesses any time, and even invite non-technical teammates thanks to the simplicity of the user interface.
6. Secret Usage Monitoring With Onboardbase
Because human errors can happen anytime, you need a way to monitor secret usage to detect any unauthorized access.
Onboardbase offers a secret usage monitoring feature that allows you to track all secret accesses in real-time. You can also set up alerts to be notified:
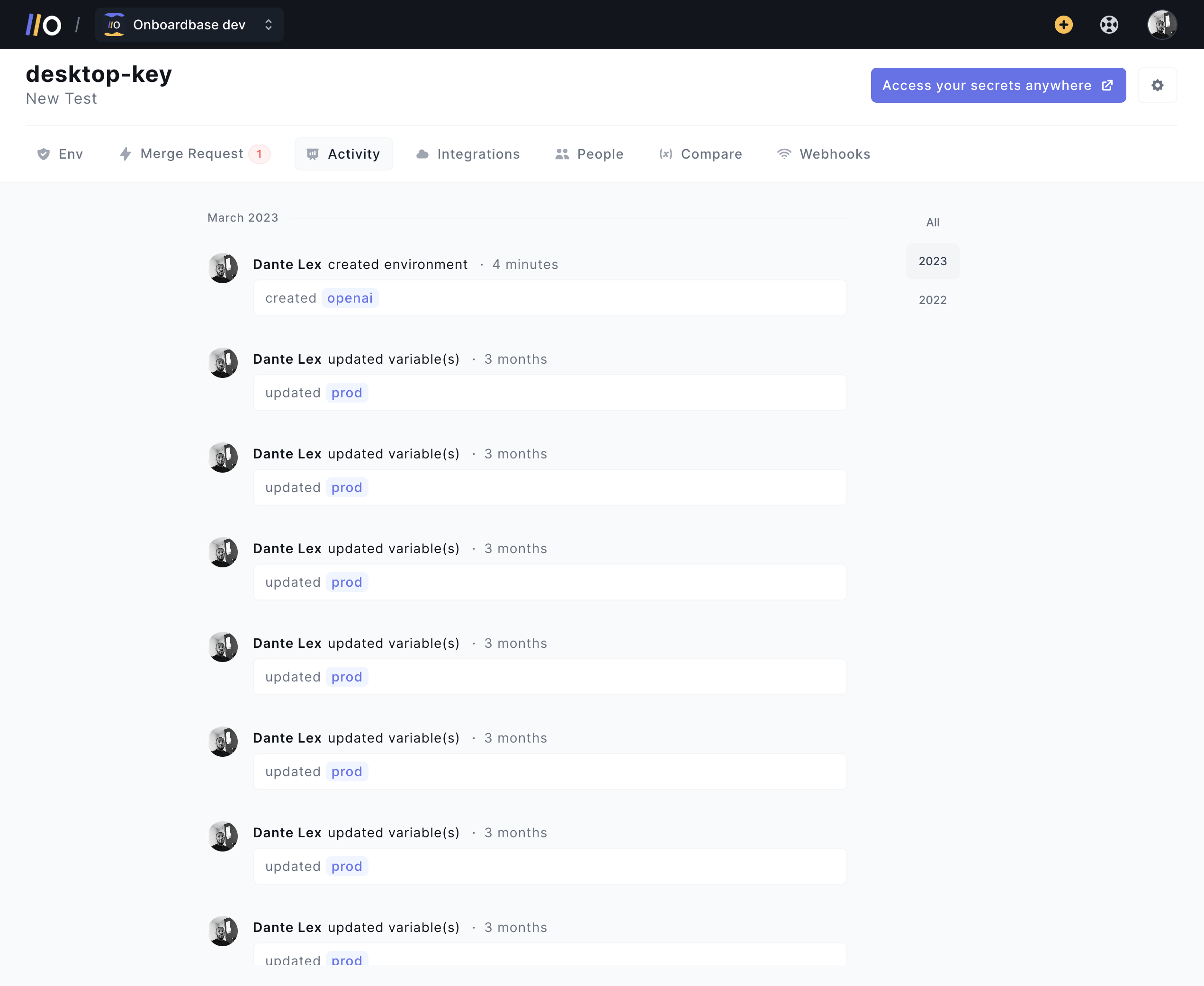
More specifically, Onboardbase offers three features in one to monitor secrets right from the web dashboard:
- Real-time monitoring to notify dev teams when, where, and how secrets are being used. In case of data breaches, you can revoke accesses granularly in an instant.
- Device management to keep track of all tools, cloud services, and devices connected to a project workspace, as well as a feature to ban compromised devices.
- Codebase secret detection to scan codebases for exposed secret vulnerabilities. Whenever compromised code is detected, the scanner prevents it from being pushed to production.
You don’t need to do anything specific to enable those, just log in.
Manage Secrets With Onboardbase
Secret management can be divided into 6 parts, but you only need 4 tools to handle all of them and 3 out of 4 are free.
Onboardbase takes care of 80% of your secret management needs, and it’s free to get started! Thanks to a convenient CLI, it only takes a minute to integrate Onboardbase in your repository and import your secrets. And you can onboard the whole team in the web dashboard in a few clicks.
If you liked this article or have any questions, feel free to reach out to us on Slack. We’re always happy to help!
Subscribe to our newsletter
The latest news, articles, features and resources of Onboardbase, sent to your inbox weekly