
Secrets Management: 6 Best Practices You Can Do Now

Toyota recently revealed hardcoded secrets have been publicly available in a GitHub repository for 5 years without anyone noticing. And it’s not the only time this sort of incident happens, even at big companies: Samsung and Nvidia, earlier this year, faced the same problem. In all these cases, security leaks originate from a human mistake caused by improper secrets management practices.
Nobody wants to be the Github contributor who cost tens of thousands of dollars to Toyota, and it is our mission at Onboardbase to make it easy for developers to work with environment variables in a secure and productive way, and that involves protecting secrets. Mistakes happen and should be accounted for. In the following articles, we explain best practices to manage secrets without anxiety.
What’s Secrets Management
A secret is a sensitive piece of data used to access or configure a software service. For example, you need an email and a password to log in an application and perform actions―these are secrets!
Secrets management is about where we store these secrets, how to make them secure, and who has the permission to have access to and manage the secrets. It’s a whole system encompassing the entire software development lifecycle that shouldn’t be taken lightly.
Why You Need Secrets Management
What we notice is how secrets are central to daily operations of any software business, and how overwhelming they can get when the complexity of modern applications never cease to increase. It is not surprising human mistakes occur in these conditions. According to a CYDEF article, employees click on phishing emails because distractions are everywhere, and that’s why it’s easy to forget to protect a secret environment variable: secrets management is essential to the well being of your team, because it decreases the possibilities of human-made errors to redirect mental energy where it matters.
Making sure your user data is safe is a legal requirement. For example, the General Data Protection Regulation in the European Union presents obligations you probably need to comply to, and failing to do so will cost you more than having proper tools in place.
As we saw it with Toyota, Samsung or Nvidia, improper secrets management leads to security leaks. And what does it say about your brand? When they use your producs, your customers trust you with their data. Failing their trust is a sure way to get put out of business. Bad PR means churn and decreased acquisition rates. Security is not just a nice-to-have investment, it’s part of your core user experience.
6 Secrets Management Best Practices
1. Never hardcode secrets
This is the number one reason secrets end up in remote repositories if you are not paying attention.
Say your application needs to connect to a Postgres database:
const sequelize = new Sequelize('postgres://username:[email protected]:5432/dbname')Instead of having sensitive information like passwords and database endpoints in plain view, put them in environment variables.
For your development environment, you can use a .env file. But don’t store it in your repository (add .env to your .gitignore file) and define environment variables in your operating system in staging or production. Otherwise you risk leaking secrets if the .env file ends up in a public folder for anyone on the Internet to see. Example:
DATABASE_USER="userName"
DATABASE_PASSWORD="greatPassWord"
DATABASE_CLUSTER="clusterName"And that’s how you would use them in NodeJS :
require('dotenv').config();
dbUser = process.env.DATABASE_USER;
dbPassword = process.env.DATABASE_PASSWORD;
dbCluster = process.env.DATABASE_CLUSTER;
const sequelize = new Sequelize(`postgres://${dbUser}:${dbPassword}@${dbCluster}:5432/dbname`)2. Make it easy to use secrets
It’s easy to feel overwhelmed by the large number of secrets your application requires to work. And it’s even more overwhelming when secrets are scattered in different places, owned by different teammates. Sharing secrets over Slack or email isn’t secure at all, so you want a system to inject secrets in your program at run time without any manual intervention.
Tools like Onboardbase or Github Secrets allow teams to centralize secrets in one place that’s easy to access to everyone, without compromising on fine-grained accesss control.
By signing up to Onboardbase, you’ll save precious time during project onboarding. Your environment variables remain consistent, and you won’t have to worry about leaking .env files because they are injected at runtime instead of being stored in files. Create as much projects as you need, and seamlessly manage secrets:
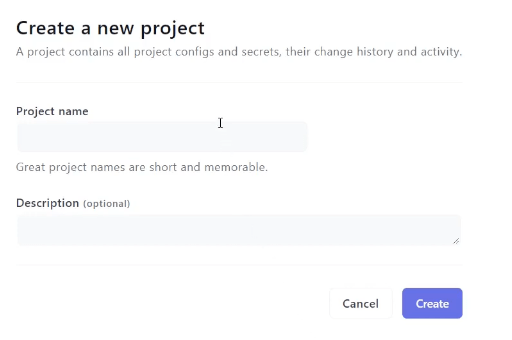
Once you have created a project, you can upload your .env file or add secrets manually:
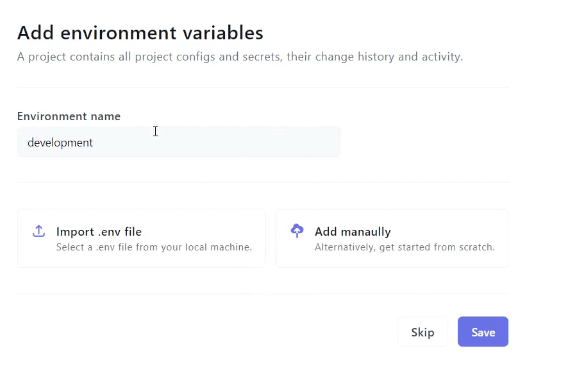
If you suspect you might have spilled environment variables in your codebase, you can also use our scanning tool via the Onboardbase CLI:
onboardbase scanWhen you create a project and invite your teammates, you can all work in a shared environment. With our Merge request system, your teammates can add new secrets to the project for review, like a pull request for secrets. This way you can make sure your environment variables are always synchronized and up-to-date. Here’s an example of a merge request via Onboardbase CLI:
onboardbase recommendation:create -p [PROJECT NAME] -e [ENVIRONMENT] -n [RECOMMENDATION NOTE] [SECRETS]Now back on the Onboardbase portal, project admins can review the recommandation and accept it or reject it :
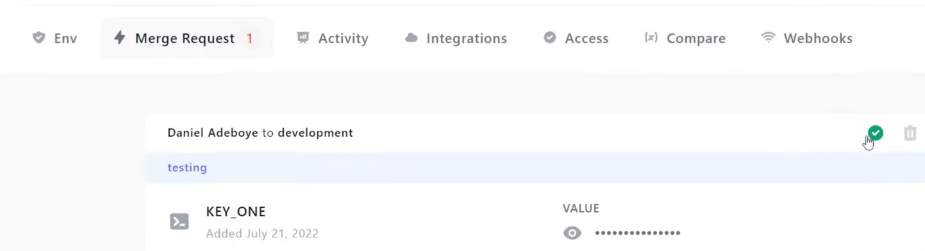
3. Manage the accesses of your secrets
With all your secrets in a single place, it is essential to manage accesses and keep track of each secret’s usage to avoid privilege escalations. By design, Onboardbase applies a principle of least privilege to all environment variables: your teammates will only be able to access the bare minimum subset of your secret database to do their job.
Managing accesses is easy. All you have to do is create a project and you’ll be able to invite any teammate:
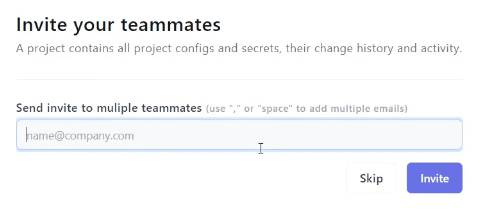
You can then create teams within each project with their own authorization policy, and this way you decide which secrets is accessible to which teammate.
Onboardbase makes it simple to store your secrets in one centralized place without creating a single point of failure.
4. Be prepared for leaks
No matter how much you’re prepared, leaks are always a risk. Monitoring the usage of your secrets is key to figure out where things went wrong so that you don’t spend hours debugging.
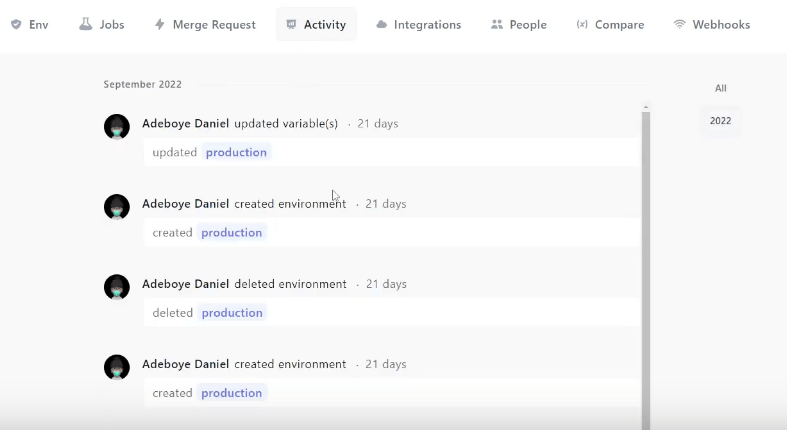
With Onboardbase, you can then watch the usage of your secrets by project―where and when they were used―in the “Jobs” section of your dashboard:
And what is new in the “activity” section:
5. Vault Encryption
Secrets should be encrypted whenever they are at rest. Pretty straightforward. Onboardbase encrypts all secrets with AES-256 at rest and RSA + AES-GCM + TLS during transport, so that you can focus on your projects instead of worrying about security. Read more about our security guidelines for more details on how we handle data.
AES stands for Advanced Encryption Standard and is a well-known standard symetric key algorithm used to encrypt and decrypt secrets. Read our article on AES encryption on our blog for much more details.
We also implement perfect forward secrecy by combining RSA, AES-GCM, and HTTPS to prevent person-in-the-middle attacks. This means Onboardbase can securely send and receive secrets to / from your projects, even on insecure networks. You can read more about that in our article on Perfect Forward Secrecy.
6. Use machines to automate secret management
Last but not least, having a tool that automates all aspects of secret management to prevent human errors is the surest way to protect secrets since humans are the n°1 cause of security leaks.
Onboardbase offers features designed to relieve you from the pain of thinking about not leaving a secret credential in your work, but you can also roll out your own custom CI/CD workflow to inject secrets at runtime. Just remember there is more to secret management than simply DevOps.
Use Onboardbase To Manage Your Secrets
Leaking secrets is not directly your teammates’ fault but rather a lack of systemic approach to good secrets management. By using the right tools, you can help your team adopt better pratices.
Onboardbase makes developers’ lives easier by making sharing and integrating environment variables simple and delightful. The best part? You can get started for free in a minute.
Subscribe to our newsletter
The latest news, articles, features and resources of Onboardbase, sent to your inbox weekly