Introducing Secure Log (2023): A Secure Console.Log Alternative In Typescript

We’re excited to introduce one of our first open-source contributions: secure log.
Secure log is a better and more secure Javascript console.log experience that detects and prevents leaking API tokens and other app secrets into your logs.
We all love debugging our code with console.log: it’s easy, fast, and you can just move on with your day without much friction. But what if you forget to remove your console statements from your code in the heat of the moment? In the worst case scenario, you can leak sensitive information attackers can use to target your customers.
Secure log solves that: it’s Javascript’s console, with an extra security layer.
It doesn’t disrupt your dev team’s favorite workflow, but protects them from tiny mistakes that can cost a fortune.
What’s console log
In JavaScript, console.log() is a built-in function provided by web browsers and Node.js environments that allows you to output messages or data to the browser’s console or the terminal. It is commonly used for debugging and understanding what’s happening in your code at different points during execution.
The syntax for console.log() is straightforward:
console.log(value1, value2, ..., valueN);It’s a useful tool for developers when they want to inspect variables, check if certain code blocks are being executed, or simply log messages for debugging purposes. But it’s not recommended to leave console.log() statements in your production code since they can affect performance and may expose sensitive information.
Why you need secure logging
Secure logging prevents secret leaks and sensitive data exposure. Without proper monitoring mechanisms, valuable information like passwords or API keys might accidentally find its way into log files, posing a severe security threat.
To prevent data breaches, it’s important to install vulnerability and compatibility scanners. These tools help identify potential weaknesses and vulnerabilities in the application, enabling you to proactively address them before they are exploited by malicious actors. Secure log acts as a vulnerability scanner for your console.log statements without introducing a new tool in your tech stack.
App and server misconfigurations can also lead to unintended exposure of sensitive data if you print app details in the console. Therefore, preventing your logs from exposing sensitive information is crucial to maintaining a secure application. If you leave console statements in your code, injection attacks like SQL injection or code injection could be used to display your app state as well, which can then be used to escalate the attack.
In production environments, leaving console.log() statements with sensitive data could end up in production logs, posing a significant security risk if the logs are accessed by unauthorized individuals.
Lastly, logging statements can have a negative impact on the performance of your application when they often arise. While it may seem like a harmless statement, it can add unnecessary overhead, especially if you have logging statements in a frequently accessed loop. This can slow down your application and potentially cause denial of service errors.
How to use secure log
SecureLog works in both Node.js and the browser. It only takes two lines of code to override the default console:
import SecureLog from '@onboardbase/secure-log';
new SecureLog();You can then use your console methods as usual:
console.log('Hello world!');The logs will include the SecureLog prefix.
You can also add a configuration object to disable logging in certain environments. For example, to disable logging in production:
new SecureLog({
disableOn: 'production', // disables the securelog wrapper
disableConsoleOn: 'production', // disables logging
});The environment names must match the ones in your process.env.NODE_ENV environment variable.
The SecureLog library parses the arguments passed to the console.log function to check if any of the ...args inside your console.log function is a secret defined in your environment configuration. The parser throws a warning if any potential secret is found. For example:
console.log('secret', process.env.AWS_ACCESS_KEY_ID);This statement will throw a warning if an actual AWS_ACCESS_KEY_ID is found in the process.env to notify the user that they are logging a potential secret. You can then use this warning in your CI/CD pipeline to prevent the code from being deployed.
Supported console methods
The SecureLog library supports the following console methods.
console.log
Logs messages to the console.
console.log('Hello world!');console.clear
Clears the console of any previous log messages and outputs.
console.clear();console.warn
Logs a warning message to the console.
console.warn('Warning!');console.profileEnd
Stops the current profiling session and displays the collected profile data.
console.profileEnd();console.debug
Logs debug messages to the console, often used for debugging purposes.
console.debug('Debugging!');console.info
Logs informational messages to the console.
console.info('Info!');console.error
Logs error messages to the console.
console.error('Error!');console.table
Displays tabular data as a table in the console.
console.table(['a', 'b', 'c']);UNSUPPORTED METHODS
- console.assert
- console.count
- console.countReset
- console.dir
- console.dirxml
- console.group
- console.groupCollapsed
- console.groupEnd
- console.markTimeline
- console.profile
- console.time
- console.timeEnd
- console.timeLog
- console.timeStamp
- console.trace
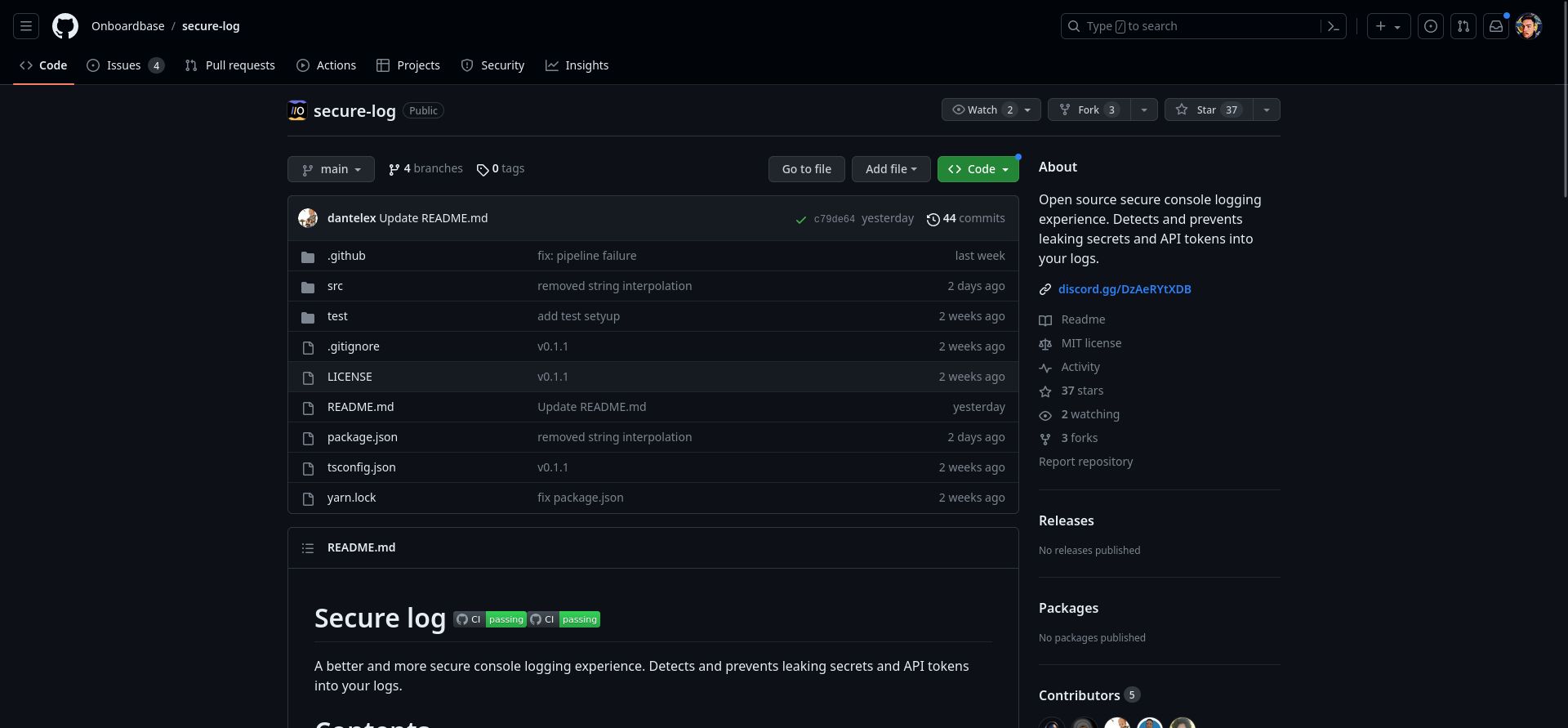
Codebase tour
Secure log is a Typescript wrapper around the console object that checks you don’t leak env secrets in your codebase by matching .env variables with console calls:
- It extends the native console object in a SecureLog class. Even though you can find online discussions entertaining the idea of overriding console methods, it is bad practice because it can break other parts of your application that need it.
- Unsupported methods will fail gracefully with a console error message.
- The library is type-safe and tested.
The program fits in a single file, so feel free to have a look and contribute!
Conclusion
Download the program from our Github repository and make sure to join our Discord community. We’ve got some good stuff on the roadmap:
- Install SecureLog via CDN
- AI to scan values passed to
console.logand report potential sensitive logs
Our ambition at Onboardbase is to become the go-to platform for developers to build and ship secure applications. We’re starting with a simple library that can help you prevent sensitive data leaks in your logs, but we have a lot more in store for you. Stay tuned!
Subscribe to our newsletter
The latest news, articles, features and resources of Onboardbase, sent to your inbox weekly