
State Of Startup Cybersecurity Report (2023): Key Stats, Main Threats, Solutions & Opportunities

Cybersecurity is the practice of protecting software systems from unauthorized access, theft, and damage. It’s an essential aspect of any organization’s operations, including startup companies. While founders may underestimate the risks of cyber threats because they are too busy growing a company, it’s important to understand that startups are great targets for cybercriminals: they have weaker security measures than established companies, they store valuable data, and they sometimes have access to significant funding. Cybersecurity is no joke: a breach will have severe consequences for a startup, including financial losses, damage to the company’s reputation, and legal liabilities. The cost of a breach is devastating and can lead to failure.
It is critical for startup founders to prioritize cybersecurity and implement robust security measures to protect their digital assets and safeguard their company’s future. But where do you start? This guide based on OWASP’s Top Ten will help you understand the most common cybersecurity threats and how to protect yourself from them in an effective, realistic way for a startup. Don’t wait until it’s too late!
Key Stats
- Bigger companies tend to have higher security standards: 50% of large enterprises spend at least $1 million per year on cybersecurity - Cisco
- Fixing a data breach in less than 200 days can save $1.12M on average - IBM
- Smaller companies spend less than $500 per year on security - Juniper Research
- Stolen credentials are the most common cause of data breaches, while taking 327 days to identify on average - IBM
- Phishing attacks come second with 37% of all cyberattacks, so education is key - Statista
- Nobody is safe: 56% of organizations have experienced a security breach in the past year - Cisco
- A data breach costs an average of $4.35 million, and twice the amount in the US - IBM
1. Distributed Denial Of Service
DDoS attacks increased by 74% in 2022 compared to 2021, targeting startups in all industry sectors.
A Denial of Service (DoS) attack disrupts a web application by overwhelming it with traffic requests to make it unavailable. DoS attacks can be particularly harmful to web startups, as they can easily cripple your systems and cause significant financial losses.
Prevention Checklist
- Rate limit your web server endpoints - In your reverse proxy configuration, add a rate limit policy to prevent spam requests on key endpoints.
- Use a load balancer - A load balancer is a reverse proxy dividing incoming traffic between multiple local web servers to prevent bottlenecks.
- Use a content delivery network (CDN) - A CDN is a network of servers located around the world to deliver web content closer to the end-users.
- Use a floating IP address - A floating IP address is an IP address that can be quickly reassigned to different web servers in the event of a security breach.
While DDoS are among the most common types of attacks nowadays, it’s also relatively easy to protect yourself from them with basic tools like Cloudflare.
2. Human Error
Insider threats mean employees or contractors leaking sensitive data. These attacks involve tricking employees into divulging sensitive information, such as login credentials, through fraudulent phishing emails, messages, phone calls, and other social engineering attacks.
Humans are always the weakest link when it comes to cybersecurity. In many cases, cyber attacks are successful because of simple human errors that could have been prevented with a little bit of preparation.
Prevention Checklist
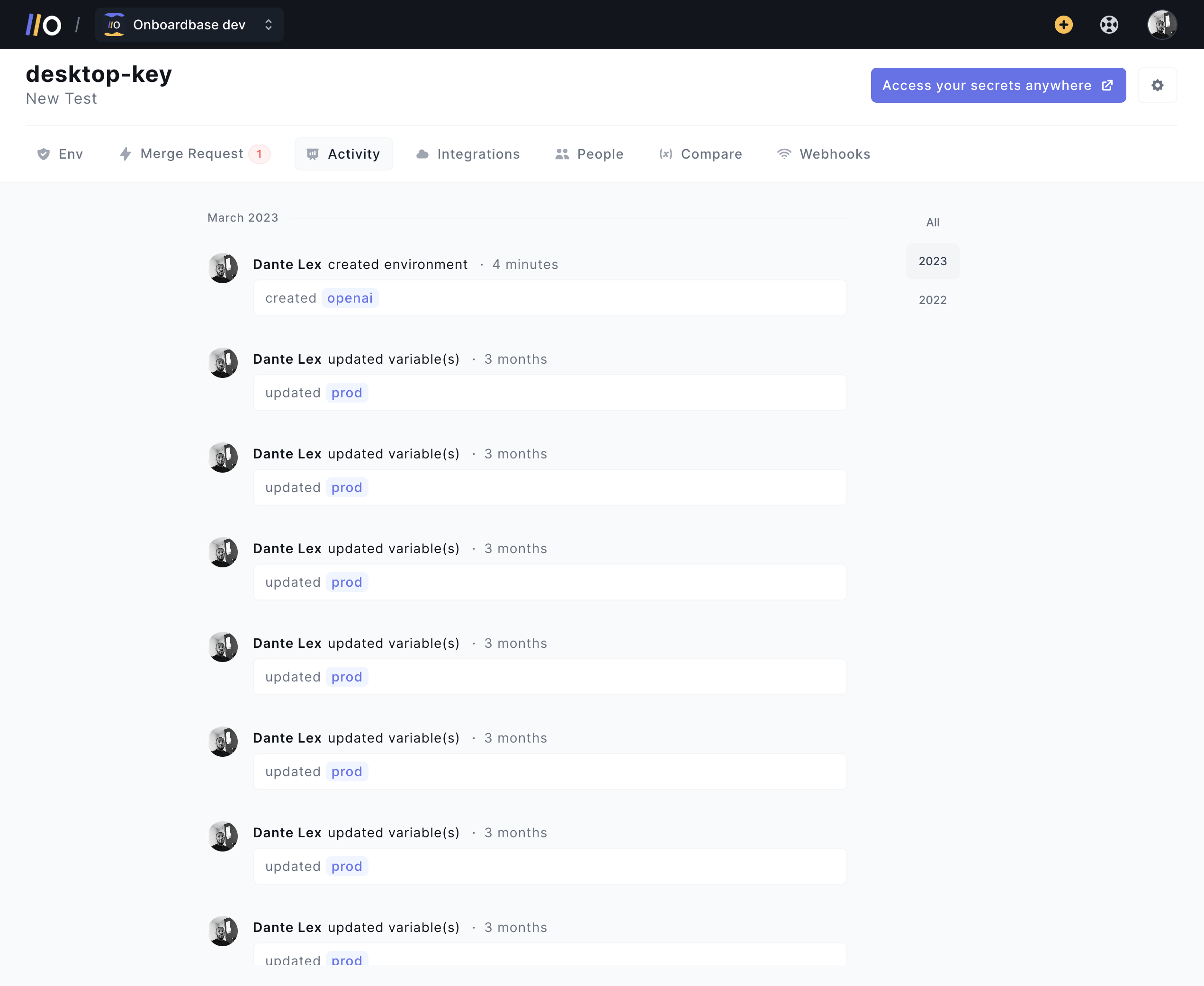
At Onboardbase, we offer a range of such systems that come as standard with our services to ensure maximum protection for our clients:
- Real-time monitoring tells dev teams where, when, and how their developement environment configurations are being used. In case of irregularities, access can be revoked instantly with just a click, minimizing the risk of security breaches.
- Device management keeps track of all devices connected to a project workspace, while allowing to revoke access for compromised devices.
- Codebase secret detection scans codebases for exposed secret vulnerabilities. If compromised code is detected, the system will prevent it from being pushed to production, ensuring that client data is always secure.
Additionally, it is important to provide adequate employee training to educate them on security best practices.
Fine-grained access control and policy management is also mandatory for all relevant stakeholders.
3. Access Control & Authorization
318k websites tested by OWASP (3.81%) had at least one critical vulnerability in their access control policies.
Authorization defines who can do what in an app, and broken access control leads to unauthorized data modification. Startups are particularly vulnerable to this as they often have limited resources and lack the expertise to properly implement and manage authorization rights: having a large number of users and stakeholders makes it challenging to ensure each one has the appropriate level of access.
Watch out for the following red flags:
- You can impersonate roles via HTTP parameter.
- You use insecure direct object reference in requests, like primary keys for example.
- You can manipulate access tokens - JWT, a cookie, or hidden fields.
- Your CORS policies allow access from untrusted origins.
- You can browse to unprotected webpages by typing their URLs in the search bar.
Prevention Checklist
Aside from testing your access control policies with unit and functional tests to make sure users can only access the records they own:
- Deny by default - Accesses should be unauthorized by default, unless the user has the relevant roles.
- Use a zero trust architecture whenever applicable - A security model that assumes no user or device is trustworthy by default, and continuously verifies all devices and users before granting access to resources.
- Don’t let users see file metadata (like .git or .env files) or backup files, and make sure web directories can’t be listed.
- Keep track of when access controls fail, and send alerts after repeated failures
- Rate limit API requests and controller accesses to reduce the risk of automated attacks.
- Make sure session identifiers are invalidated after logout and use short-lived tokens.
Using an identity management tool, whether it’s in your web development framework or a dedicated cloud service, helps to automate the implementation and maintenance of these checklist items.
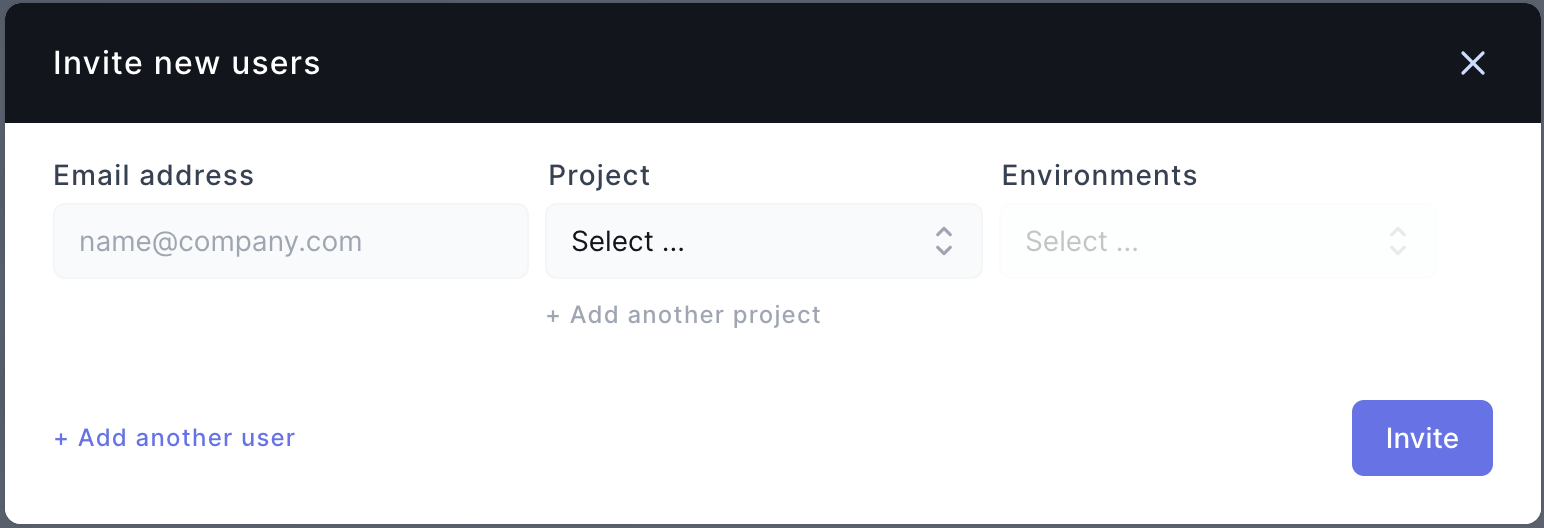
For secret credentials, Onboardbase applies the principle of least privilege and only grants access to the minimum amount of data required to perform a task. You can create teams within each project and define custom authorization rules easily. Then, just invite collaborators to specific teams and projects as needed:
4. Broken Encryption
234k websites tested by OWASP (4.49%) presented a critical vulnerability in their encryption system.
Encryption is a way to safeguard sensitive data against security breaches by transforming data into a form that is unreadable for unauthorized individuals without the proper decryption key. Applications often need to protect data in transit and at rest, but not all data have the same encryption requirements. To learn more about encryption at rest and encryption in transit, check out our dedicated articles in our blog.
Your encryption pipeline is probably at risk if you find yourself in one of the following scenarios:
- You data is transmitted in clear text (possibility of a man-in-the-middle attack)
- You use old or weak encryption protocols, including deprecated hash functions (MD5, SHA1) and deprecated padding methods
- You have weak encryption keys, either old or poorly designed
- Your website isn’t served over HTTPS, or displays an invalid certificate
Prevention Checklist
Encrypting all sensitive data at rest and in transit using appropriate algorithms is obviously the first step. You can also:
- Avoid storing data unnecessarily - delete it whenever it’s not needed anymore
- Use secure passphrases, salted hashing functions, and appropriate initialization vectors and keys.
- Use signed encryption instead of just encryption, and avoid deprecated cryptographic functions and padding schemes.
- Have a system in place for secret management
A tool like Onboardbase is important to keep your encryption keys secure in a dedicated vault you can easily call in your devops pipeline. We use AES-256 at rest and a combination of AES-GCM and RSA in transit as part of our zero trust architecture, as per our security guidelines.
5. Injection Attacks
274k websites tested by OWASP (3%) were vulnerable to injection attacks.
Injection attacks are when a hacker injects malicious code or commands into a web application by exploiting vulnerabilities in the user interface, whether it’s via form, URL, or API request. Common injection attacks include SQL injection and XSS injection, and typically happen when you process unsanitized and unvalidated user data inputs, or implement non-parameterized requests or use concatenated string parameters in queries.
Prevention Checklist
- Review the source code to detect injection vulnerabilities, and use automated testing for data inputs.
- Use application security testing tools like Onboardbase or Github in your CI/CD pipeline to catch injection flaws before deployment.
- Use a safe API, parameterized interface, or ORM to send queries.
- Use server-side input validation and escape special characters in dynamic queries.
- Be cautious with SQL structures like table and column names, and use LIMIT to prevent mass disclosure of records in case of SQL injection.
- Strong type-checking is also an effective way to secure your data logic
Most back-end frameworks offer built-in features to implement these best practices, but you also need to add checks in your front-end code.
6. Unsecure Design
262k websites tested by OWASP (3%) showed signs of unsecure design.
When creating software, it’s important to think about how to protect sensitive information from the start. It’s easy to consider security as an afterthought when you’re busy gaining traction for a new product, but it’ll be costlier to fix this technical debt in the long run.
A typical example is password sharing tools. The ones you see on the market usually involve sending a temporary link to the person you want to share the info with, but it’s easy to see where things can go wrong: the receiver’s email can be hacked, or the link can be leaked. This is unsecure by design.
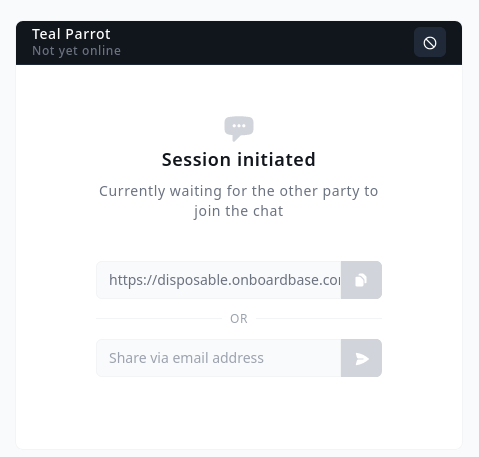
At Onboardbase, we went the other route and built Credentials.new with security-first principles instead: it’s real-time, end-to-end encrypted, and ephemeral. The messages disappear as they are read, no data is stored or retained, and all transmissions are encrypted. No traces! Ultimately, these early design decisions allowed us to build something that’s truly secure, unlike our competitors.
Prevention Checklist
- Use a secure development lifecycle that integrates security best practices into the development process, with devops for example.
- Leverage libraries of secure design patterns and components
- Identify potential security threats and create a plan to prevent them
- Integrate security requirements into user stories to cover all stakeholders
- Write unit and integration tests to validate that all critical flows are resistant to threats described in this article.
- Always limit resource consumption by user, like rate limiting for server calls
Unsecure design is a by-product of poor knowledge regarding security best practices―communication with experts and users is key to taking into account all possible scenarios!
7. Security Misconfiguration
Security misconfigurations concerned 208k websites tested by OWASP (4%).
Misconfigurations can create vulnerabilities for attackers to exploit. A typical example is Toyota exposing the sensitive information of 300,000 customers in September 2022, by leaving an access key in a GitHub repository for almost five years. This is a classic misconfiguration mistake: you push secrets in a git repo by not adding your .env file to your .gitignore configuration file, and it’s now forever engraved in your commit history.
You are likely at risk if you:
- Use improperly configured permissions
- Enable unnecessary features (e.g., ports, services, pages, access roles)
- Use default accounts and passwords
- Send overly informative error messages to users
- Do not send server security headers
- Use outdated or vulnerable software
In 2022, vulnerabilities in third-party software were responsible for 13% of known breaches, according to IBM, and cost $4.55M per data breach on average.
Prevention Checklist
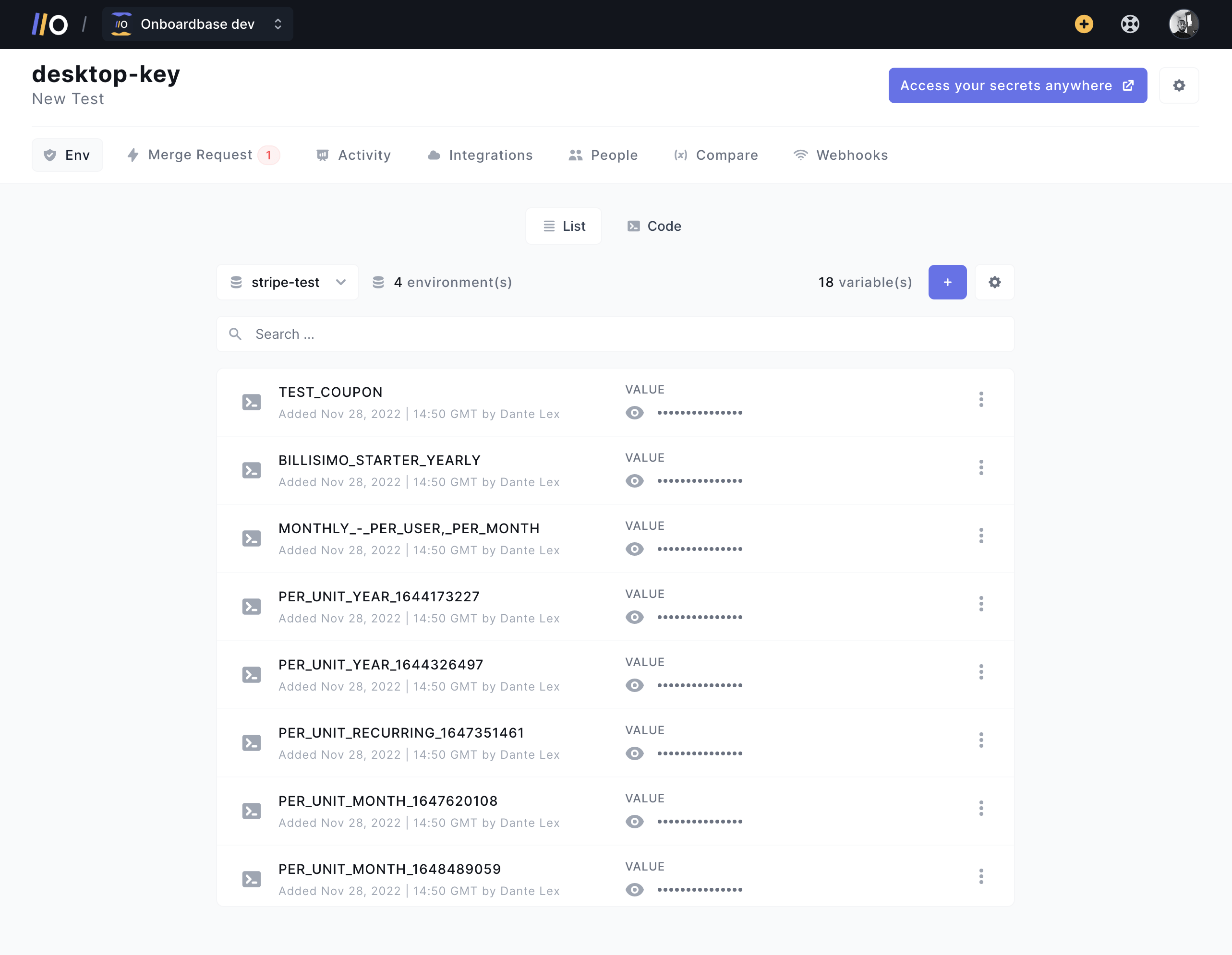
- Use a CI/CD pipeline to automatically deploy secured environments
- Use Onboardbase to inject environment configurations at build or deploy time
- Remove unused code
- Review configurations, security patches, and access permissions regularly
- Use segmented application architecture to avoid single points of failure, using segmentation, containerization, or cloud services
- Send server security headers
- Test and validate your environment configuration before deploying using automated tests
- Install vulnerability and compatibility scanners
A solution like Onboardbase that removes the need to use environment files entirely is key to keeping your developer team productive without compromising on security: just use the onboardbase init command to walk you through all the steps you need to get started with Onboardbase in less than 5 minutes in any development workflow.
8. Authentication
Authentication issues occured in 132k websites tested by OWASP.
Authentication is the process of verifying the identity of a user: you go through an authentication process every time you log in with an email / password pair, for example. Authentication usually goes hand in hand with authorization (access control), but they aren’t the same. Authentication asks who is who, while authorization defines who can do what.
Typical authentication mistakes junior web developers do include:
- Allow default, weak, or well-known passwords, opening yourself to credential stuffing and other brute force attacks
- Weak credential recovery process like knowledge-based questions
- Store plain text passwords
- Single-factor authentication
- Exposed session identifier in the URL
- No invalidation process for Session IDs, or long session duration
Prevention Checklist
- Use multi-factor authentication whenever possible to prevent attacks that try to steal your login info.
- Don’t use default login credentials, especially for admin users.
- Check passwords for strength and ensure that they are rotated regularly.
- Make sure that registration, credential recovery, and API endpoints are secure against hackers trying to guess login info.
- Limit the number of failed login attempts and log all failures, so you can detect and respond to attacks.
- Use a secure session mechanism that generates a new session ID after login, keeps it private, and invalidates it after logout or timeouts.
Just like authorization, authentication is best handled by a third-party service if you do not have the resources to implement and maintain a strong security protocol.
9. Monitoring Failure
OWASP tested 53k websites failed to monitor their security.
Monitoring tools track HTTP traffic and performance in real-time to find odd patterns that could lead to a security breach. HTTP monitoring consists in setting up CRON jobs on a web server that will send HTTP requests and test the responses. Log monitoring leverages your web server’s logging feature to analyze traffic and find errors.
To help detect, escalate, and respond to active breaches. Without logging and monitoring, breaches cannot be detected. Insufficient logging, detection, monitoring, and active response occurs any time.
Toyota, once again, comes to mind as a perfect example when it failed to detect a secret leak in a public Github repository for 5 years.
Typical threats:
- Events like logins, failed logins, and high-value transactions, are not logged
- Warnings and errors generate no clear log messages
- Logs of applications and APIs are not monitored for suspicious activity, and there is no alerting feature or escalation process in place
- Logs are only stored in your web server’s hard drive
- Penetration testing and scans do not trigger alerts
- Logging and alerting events are visible to anonymous users
Prevention Checklist
- Make sure to log all events like login attempts, access control failures, and input validation errors. Include enough information to identify suspicious or malicious accounts, and keep logs for forensic analysis.
- Sign your logs to prevent tampering.
- Set up monitoring and alerts to quickly detect suspicious activity.
- Have a plan in place for responding to security incidents.
- Monitor vulnerabilities, secret usage, and codebase issues
It is advised to use external tools to avoid down time. Most web servers can log their HTTP traffic to a log file if you enable it in the settings, but you still need to export this data to a third-party tool for safe-guarding.
10. Server-Side Request Forgery
9,503 websites tested by OWASP (2.72%) were vulnerable to SSRF.
Server-side request forgery (SSRF) occurs when an attacker tricks a server into making a request to a third-party server or service that the attacker controls, usually by manipulating input parameters or exploiting vulnerabilities in the server. For example, a web application allowing users to input a URL to an image could be manipulated to point to a malicious link and potentially extract sensitive information or carry out other attacks.
The risk of SSRF keeps increasing as more and more features are outsourced to cloud services.
Prevention Checklist
- Keep remote resource access in a separate network to avoid single points of failure
- Validate and sanitize all client-supplied input data
- Use a positive allow list to enforce URL schema, port, and destination
- Do not send raw responses to clients and disable chained HTTP redirections to avoid DoS attacks
- Do not rely on deny lists or regular expressions to mitigate SSRF attacks, as attackers can bypass them by just changing their IP addresses
Another way to avoid SSRF is to ditch server-side rendering entirely: most websites can switch to static site generation to reduce attack surfaces, and authenticated web application pages can use client-side rendering. SSR is only necessary when you deal with dynamic, public-facing pages, to help with SEO for example.
11. Data Loss
Data is often your most valuable asset as a startup. Loss of data results in significant financial, legal, and reputational damages, and can also negatively impact your startup’s operational productivity.
A typical example would be for a new startup founder to forget to enable database backups, or set the backup frequency too low. Signs you need to improve your data recovery process includes:
- The database isn’t regularly backed up.
- The access control policies are misconfigured and users can delete data that do not belong to themselves.
- The backups aren’t encrypted, or use a weak master encryption key that’s easy to break.
Prevention Checklist
If you already implemented all the previous items in this article, especially the ones regarding encryption, access control, and automated testing, you have drastically reduced risks of data loss.
One thing to add would be to have a backup system that regularly makes encrypted copies of your database and distributes them offsite. If your web infrastructure is compromised, leaving copies in your local disk is a huge risk: even if your encryption keys are strong, there is a chance we reach a day where we’ll have the technology to brute force them―using quantum computing, for example.
Future Opportunities
1. AI Security
With the increasing use of artificial intelligence in various fields, the demand for AI security is also on the rise. AI security companies can develop algorithms that can detect and prevent cyber threats in real-time, as well as provide training and support to organizations.
More recently, AI also creates new attack vectors like adversarial machine learning, which can be used to trick AI services like OpenAI’s into making mistakes, or prompt injection. Machine learning models also require significant resources to run, possibly creating new ways to DDoS services leveraging AI features. AI security companies can develop solutions to prevent these attacks.
2. DevSecOps
DevSecOps is an emerging approach that integrates security into the software development process from the start. Cybersecurity companies like Onboardbase offer DevSecOps solutions to help organizations build secure applications and prevent security issues before they occur.
3. Quantum Computing
As quantum computing becomes more accessible, cybersecurity companies can offer quantum-safe solutions to protect data and systems from quantum-based attacks. Quantum cryptography and key distribution are some of the areas where cybersecurity companies can innovate.
Inversely, since we aren’t far from the first personal quantum computer, we’ll also need to start implementing new, stronger encryption systems. Current encryption systems like AES-256 are based on the difficulty of factoring large numbers, which is a problem that quantum computers can solve in a matter of seconds.
4. Blockchain Security
Despite major cases like FTX’s demise, blockchain technology continues to gain traction in various industries with a compound yearly growth rate of 56.3%, and cybersecurity experts can offer blockchain security solutions to secure blockchain networks and prevent attacks or frauds.
With healthcare and finance being both the biggest targets of cyber attacks and the biggest consumers of blockchain tech, blockchain security still has a few profitable niches.
5. Data Privacy
Data privacy is a growing concern, and cybersecurity companies can offer data privacy solutions that can protect personal and sensitive data from cyber threats and comply with data privacy regulations.
85% of Internet users want to do more to protect their online privacy, according to a study by Norton: this is a huge differentiator for startups who value their user experience!
Subscribe To Onboardbase
And that’s a wrap! Hope you enjoyed this article and that it’ll help you grow stronger. If you want to stay up to date with the latest cybersecurity news and trends, subscribe to our newsletter below!
Onboardbase is your all-in-one solution to build secure web applications. We offer a complete set of tools to help you build, test, and monitor your environment configurations right from your devops pipeline. Try it for yourself for free or book a demo with us if you need help to set up or for further insights on features we offer.
Subscribe to our newsletter
The latest news, articles, features and resources of Onboardbase, sent to your inbox weekly