
4 Recent Cyber Attacks Every Startup Should Learn From (2023)

For some startup teams, security is an afterthought: you need to move fast, even if you break things. But don’t get fooled, cyber threats are just as common today as yesterday, and the wrong mindset can lead to catastrophic consequences for your business. Not only will you lose customers because of breached trust, but you’ll also pay thousands, if not millions, of dollars in urgent fixes and legal fines.
At Onboardbase, we’ve seen countless startup customers use bad practices that could cost them months of runway with just one person’s mistake. We hope it won’t ever happen to you, so in this article, we’ll have a look at 4 recent cyber attacks that made headlines and what you can learn from them to keep your company safe and secure.
1. LastPass (December 2022)
In December 2022, hackers obtained sensitive information from popular password manager LastPass, including user information such as billing and email addresses, telephone numbers, and IP addresses.
They also accessed encrypted customer vault data like website URLs, usernames and passwords, secure notes, and form-filled data. If the hackers manage to crack the master password of any LastPass user, they can access their entire online life.
Key Lesson N°1: Always Enforce Strong, Unique, Encrypted Passwords
While LastPass claims it would take a million years to decrypt the master password hackers need to access the data, it’s assuming the master password contains a minimum of 12 random characters. Weak passwords, on the contrary, only take minutes to guess.
Similarly, re-using passwords from one place to another puts you at greater risk. A Google study showed 65% of all users have the same passwords on multiple sites: as a startup, it is primordial to pay attention to your password management practices.
Strong password generators are now integrated into every browser, but at Onboardbase, we go one step further with passwordless authentication: you need to click a confirmation link every time you want to access your password vault via the web browser.
Onboardbase encrypts all secrets with AES-256 at rest and RSA + AES-GCM + TLS during transport. You can read more about our security guidelines for more details on how we handle data.
2. FlutterWave (February 2023)
In February 2023, Flutterwave, the largest startup in Africa with a valuation of $3 billion, was allegedly been hit by a hack resulting in the loss of $4 million from its accounts. The cause and method of the attack remain unclear, but the main hypothesis is social engineering―the customers’ keys have been compromised, giving the hackers access to their Flutterwave accounts. Despite this, Flutterwave has denied being hacked, and there hasn’t been clear evidence of a data breach.
Key Lesson N°2: Humans Are The Weakest Link
The incident involving Flutterwave highlights the importance of taking cybersecurity seriously: humans are often the weakest link when it comes to cybersecurity. In many cases, cyber attacks are successful because of human error, such as using weak passwords or falling for phishing scams. It is essential to educate people on how to stay safe online and to implement effective security measures that take the human factor into consideration.
Fine-grained control and access policy management should be made mandatory for all relevant stakeholders: only share the bare minimum to get work done, limit group accesses, and keep access lists updated.
Key Lesson N°3: Expect Security Leaks
Because human error is often the primary source of security leaks, it is crucial to have prevention systems in place. At Onboardbase, we offer a range of such systems that come as standard with our services to ensure maximum protection for our clients:
- Real-time monitoring enables clients to find out where, when, and how their environment configurations are being used. In case of any irregularities, access can be revoked instantly with just one click, thereby minimizing the risk of security breaches.
- Device management allows users to keep track of all devices connected to their workspace and instantly revoke access if a device is compromised.
- Codebase secret detection scans codebases for exposed secret vulnerabilities. If compromised code is detected, the system will prevent it from being pushed to production, ensuring that client data is always secure.
3. Toyota (September 2022)
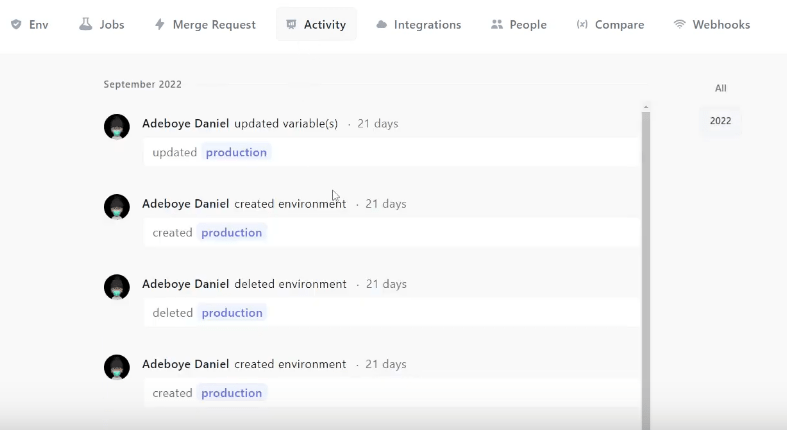
Toyota exposed the sensitive information of 300,000 customers by leaving an access key in a GitHub repository for almost five years.
Similar security breaches have been experienced by other companies like Samsung and Nvidia earlier this year. This is a classic mistake: you push secrets in a git repo―by not adding your .env file to .gitignore, for example―and it’s now forever engraved in your commit history. The most effective solution is to simply re-create all leaked secrets and login credentials.
Key Lesson N°4: Don’t Share Secrets Online
Nobody wants to be the Github contributor who costs tens of thousands of dollars by negligence. But more generally, sharing any sort of secret online is a recipe for chaos.
You can use Onboardbase to securely inject passwords and secrets in software projects as environment variables at runtime using the CLI, whether you use Github or another devops platform.
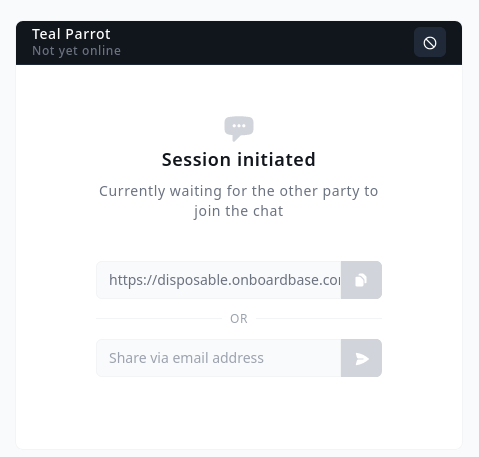
If you really need to share a secret with a colleague, use our latest product, Credentials.new: it’s a real-time, end-to-end encrypted, ephemeral communication tool for secret sharing. The messages disappear as they are read, no data is stored or retained, and all transmissions are encrypted. Github repositories, Slack channels, or emails present too many risks―better leave no traces!
4. Slack (July & December 2022)
In July 2022, Slack disclosed that it had unintentionally exposed hashed passwords for five years: when users created or revoked a shared invitation link for their workspace, it would contain their hashed password!
But that’s not the only incident. In December 2022, Slack detected suspicious activity on its GitHub account, and the security team discovered that some employee tokens had been stolen and used to access the company’s external GitHub repository. Fortunately, this incident did not impact any customers.
In both cases, a few things come to mind:
Key Lesson N°5: Never Keep Environment Config In Github Repos
As previously mentioned in Toyota’s case, it’s absolutely vital not to mix environment files with git repositories: you never know who will access your git repository!
A solution like Onboardbase that removes the need to use environment files entirely is key to keeping your developer team productive without compromising on security: just use the onboardbase init command to walk you through all the steps you need to get started with Onboardbase in less than 5 minutes.
Key Lesson N°6: Regularly Rotate Encryption Keys
Regularly rotating encryption keys is crucial for startup companies to increase the strength of encryption algorithms. Encryption keys that remain static for extended periods can become vulnerable to brute-force attacks, particularly with new advancements in computing power like quantum technology.
Similarly, it’s a good practice to have your employees change their passwords once a year or so.
Key Lesson N°7: Enable 2FA
Another way to mitigate risks of password leakage is to enable two-factor authentication. Check out our article on how to implement multi-factor authentication with Google Firebase Auth.
5 Additional Security Best Practices Every Startup Needs
There are a number of other things you can do to help mitigate security risks:
- Regular Security Audits - Startups need regular security audits to identify vulnerabilities in their systems and networks. If you plan to sell software that handles sensitive data or engage in enterprise deals, it is strongly recommended that you obtain SOC 2 Type 2 certification. This certification is a significant hurdle to overcome, but it will help you build trust with potential customers and investors.
- Employee Training - Because cyber attacks are often due to human errors, it’s crucial to provide regular cybersecurity training to employees to educate them on the importance of security measures―avoid sharing passwords, recognize phishing attempts, report suspicious activity, etc.
- Incident Response Plan - In the event of a cyber attack, an incident response plan can help respond quickly and effectively to minimize the impact of the attack. The plan should outline the steps to be taken and who to contact to restore normal operations.
- Cyber Insurance - Cyber insurance can help mitigate the financial impact of a cyber attack. A security breach can cost thousands, if not millions of dollars!
- Protect your servers - In a tech startup, your servers represent the largest surface of attack. Basic web security know-how can go a long way to thwart common attacks like DDoS or SQL injections.
If you run a SaaS startup, you might also want to have a look at our SaaS security checklist.
Secure Your Startup With Onboardbase
Even established companies can suffer from security breaches. As a startup, you are even more at risk, and you probably have more to lose. Onboardbase offers startups a powerful tool to secure their sensitive information and protect themselves from common cyber threats.
Prove your commitment to your users by not failing their trust: Onboardbase is an essential tool for any startup that values the security and integrity of their data. Get started for free in a minute.
Subscribe to our newsletter
The latest news, articles, features and resources of Onboardbase, sent to your inbox weekly